The 3 IoT Security Fundamentals Startups Need to Know

An enterprise healthcare business faces risk and privacy considerations every day. However, in a startup environment, when funding sources—or lack thereof—are looming every day, security might not be on the top of your mind.
The bad news is, you’re not alone: Research found only 40% of service providers said they were preparing for a breach within the next two years. That means 6 out of every 10 providers aren’t really preparing for a crack in the system...the system your IoT product may run on.
So, if the big guys aren’t tackling IoT security, why should an independent creator or startup care? Because, research also shows that nearly 2 in 3 people will reconsider a product purchase if data isn’t safe. If a breach does happen, that bad PR can damage the brand of your product during your crowdfunding campaign as well as long after.
To ensure that your voice-controlled speaker or connected smart doorbell isn’t leaving backers high and dry, consider these three things:
1. Security = identity in the IoT
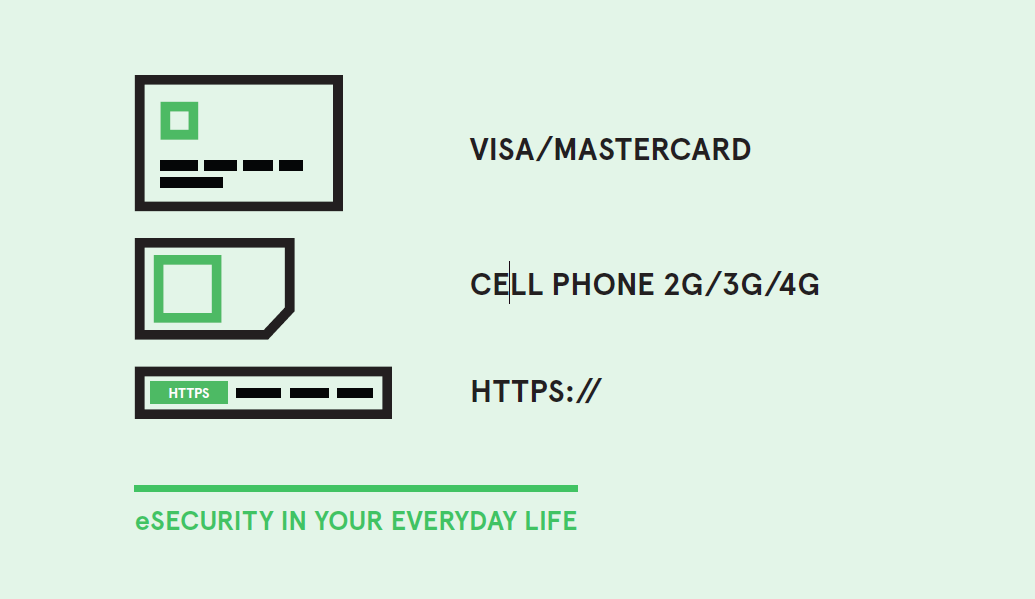
Think of IoT identity like a passport. When you get off the plane in Montreal or Mumbai, your passport verifies your identity as a citizen without customs having to do an extensive background check on every person getting off every plane at every terminal in the airport. As the saying goes, “Trust, but verify.”
Secure elements—such as the security chip in a bank card that verifies validity—are the passports of IoT, giving every single device and server it is connecting into a way to trust and verify its parts.
2. Ensure mutual authentication and message integrity, confidentiality
Once a message is identified, it still needs to adhere to three standards:
- Mutual authentication: Verifying each device or server by its true and unique identities.
- Message integrity: Trusting messages sent between devices and servers aren’t able to be hacked, altered or changed by an interfering party to ensure data integrity.
- Message confidentiality: Ensuring confidentiality of communications so only the right people can see the data in your IoT solution.
3. When you customize, you complicate
There is no one-network-fits-all technology to accomplish end-to-end security for consumer electronics today, which means all the customization you implement to make your product unique also means a lot of places where things can go wrong.
In most of the consumer products startups are creating, connected devices do less talking to each other and more reporting either on the edge of the cloud or in the cloud itself via many layers of networking. Because of this, network security alone can’t do the whole job. That’s why real and efficient IoT security should mimic internet security, and span end-to-end from device to servers.
What’s more, software-based only security won’t cut it. Unlike hardware, software can be modified, overwritten and duplicated. Efficient IoT security therefore relies on hardware roots of trust—components that perform specific security functions—speaking standard widely used protocols that due to their omnipresence can be immediately noticed, proofed and corrected.
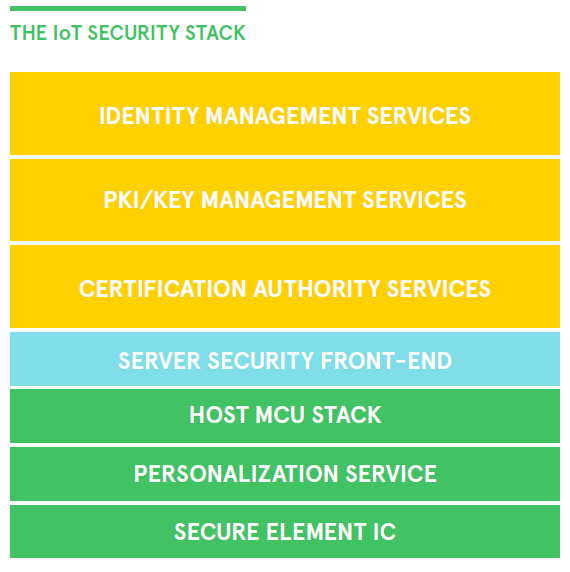 What to do next to secure your startup’s IoT solution
What to do next to secure your startup’s IoT solution
The only thing we know for good about what we are deploying today is that it will need fixes and upgrades in the future. The good news is, all you need to do to get started is find what’s free to you and begin to implement it.
You’ll need to keep this article handy, though, as you further define your product and get ready for production. Ensure if you engage with a partner that during a pre-production run, they can prove out security protocols even at very limited volume with at a very low cost. When designing for manufacturability and scale, have the same check-in.




