DefAero Mitigating Cyber Attacks MCU Hardware Accelerators Boost 2CP

Over the years, cyber attacks on financial institutions and news organizations have garnered the lion's share of attention with their threats of financial loss and exposure of confidential information. More quietly, however, reports on successful penetration of transportation and public infrastructure systems have revealed a more insidious threat arising from a pervading weakness in the security of deeply embedded designs built to monitor and control these systems. Built to counter this threat, hardware security accelerators integrated in processors enable developers to take an essential first step in mitigating threats in embedded designs.
Networks of ubiquitous, richly interconnected devices -- as envisioned in the Internet of Things -- present significant risks for attack and malware penetration. Although cyber security remains a moving target, the most fundamental tool for hardening interconnected embedded systems remains the use of encrypted communications.
Until recently, cryptographic methods underlying encryption and decryption were limited to software solutions or cumbersome standalone crypto units. In fact, software solutions offered a reasonable approach while the industry explored alternative cryptographic algorithms. With their acceptance as national standards in FIPS 197 and worldwide standards in ISO/IEC 18033-3, ciphers such as Advanced Encryption Standard (AES) now form the underpinnings of hardware-based security features in processors from leading MCU makers.
Dedicated fully to execution of crypto algorithms, these hardware accelerators provide the performance needed to enable near real-time secure communications. While no replacement for KG crypto boxes in highly classified mission-critical systems, these MCU accelerators can handle the encryptions, decryptions and mathematical computations typically required for MCU-based applications. Just as important, these dedicated security engines operate independently of the main processor, largely allowing the main CPU to be dedicated to applications processing. For the embedded application, the result is faster execution in combination with heightened security.
Although it is the dominant cipher by virtue of ISO/IEC 18033-3, AES is only one of several ciphers, authentication algorithms and security protocols supported by MCU hardware acceleration units. For example:
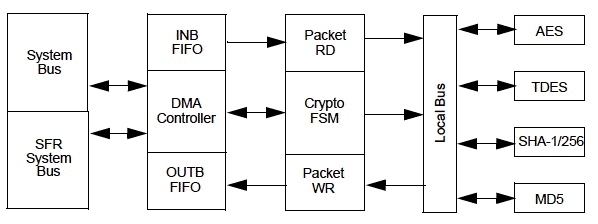
- Microchip's Crypto Engine includes four different cryptographic security engines designed to accelerate the computation of public/private key pair negotiations, message hash authentication and bulk data encryption/decryption (Fig. 1). Able to operate in parallel or daisy-chained to execute more sophisticated security methods, the Microchip Crypto Engine includes engines for AES, Data Encryption Standard (DES) and Triple DES (TDES), Secure Hash Algorithm (SHA-1 and SHA-256) and Message Digest 5 (MD5). Built into MCUs in Microchip's 32-bit PIC32MZ Embedded Connectivity Family, the Crypto Engine includes a DMA controller for scatter/gather data fetching and an intelligent state machine to schedule the individual security engines independently of the PIC32MZ's primary CPU.
- NXP offers similar capability within its Kinetis line, including a range of crypto accelerators targeted for specialized applications. For example, integrated in its QorIQ line of communications processors, a crypto accelerator supports security algorithms including RSA, Diffie-Hellman and Elliptic Curve, among others commonly used with communications standards such as IPSec, 802.1ae, SSL/TLS, SRTP, 802.11i and 802.16e.
- Indeed, dedicated security engines are becoming more readily available with a broad range of capabilities and features. Designers can find dedicated security features in more conventional processors as well. For example, Intel includes its Intel® Advanced Encryption Standard New Instructions (Intel® AES-NI), an encryption instruction set that improves on the Advanced Encryption Standard (AES) algorithm and accelerates the encryption of data in the Intel® Xeon® processor family and the Intel® CoreTM processor family.
Mitigating cyber attacks requires more than secure communications. For any embedded design, however, the ability to ensure communications integrity and access by authorized entities is a necessary start. Integrated in MCUs, dedicated security engines enable that first necessary step toward more comprehensive systems security.

